How to use Qt WebAssembly – The Complete Guide with demo
Hey, welcome back to another blog post. Today we’re going to talk about the new Qt WebAssembly. This post will […]
Join us at Qt C++ Warsaw Meetup - 21.08.2025
Sign up for free!
There is quite a noise currently around cybersecurity topics not only in terms of medical devices but generally in the world of connected devices. Security management has become a hot topic due to the implementation of the EU CRA. That’s definitely for good but the topic of cybersecurity risks was known to medical device manufacturers a long time before as it’s a standard for a long time.
You don’t have to be convinced that ensuring robust cybersecurity in medical devices is key to protecting patient safety, maintaining device functionality, and achieving regulatory compliance.
This article dives into the essentials of medical device cybersecurity standards, with a focus on their role in medical software development. From understanding the key standards to addressing cybersecurity concerns, this guide will equip you with the knowledge to foster innovation and trust in the medical device industry.
Ah, and we will soon publish two other articles on a similar topic. One will cover practical tips on ensuring medical device security. So we will give you specific tasks that are part of the software development process. So this one is a great prelude to this future post.
The other one will be on EU CRA’s implications. The links will be provided here later on.
So let’s start with a short overview of the existing standards that help and even force manufacturers to manage cybersecurity risks.
IEC 62304 is a big one. It’s the framework for safe design and life cycle management of medical device software. At Scythe Studio all of the projects that we realize for our customers, are documented according to this standard. Although scary, I personally enjoy it and I am proud of the fact that our embedded medical software development offer includes this.
IEC 62304 consists of 9 clauses:
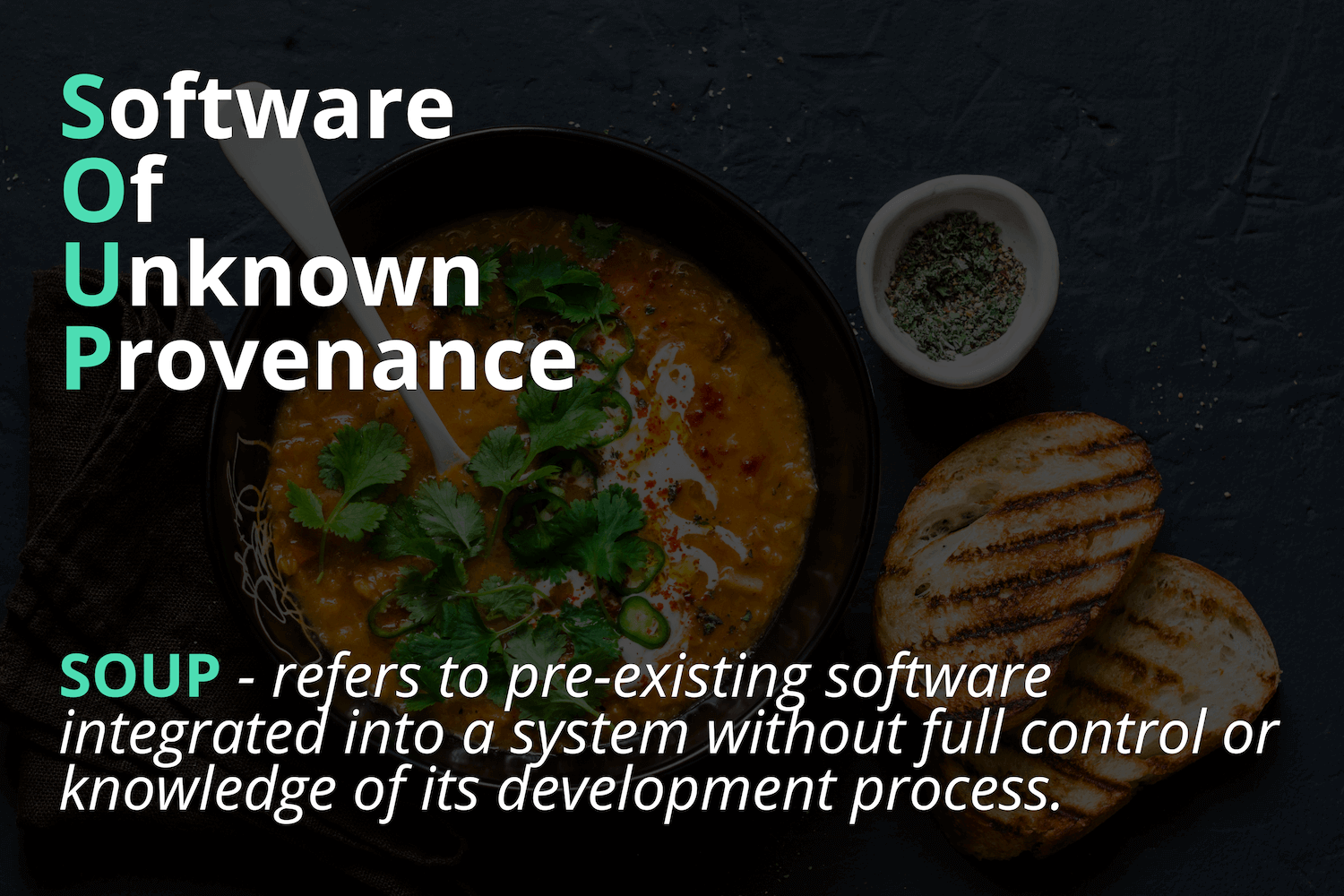 Software of Unknown Provenance
Software of Unknown Provenance
From the brief description of each clause above, you might already have an answer to this question. Yes, you all above fifth touch cybersecurity risks. Developing medical devices is complicated by definition. Ensuring high security standards is the next level making this even more difficult.
It is necessary to confront the people responsible for the technology with the regulators as early as possible. It is precisely the fact that we at Scythe understand these two worlds that makes our medical projects so successful.
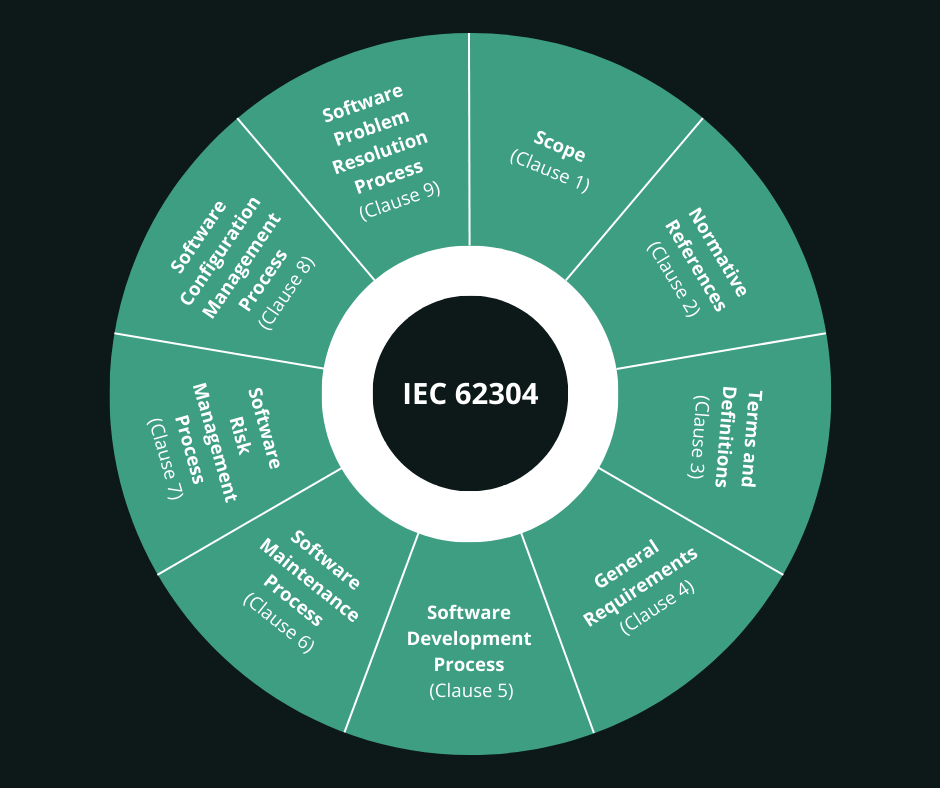 IEC 62304 consists of 9 clauses
IEC 62304 consists of 9 clauses
ISO 14971:2019 is a global standard for managing risks in medical devices. Its main goal is to protect patient safety by addressing risks throughout a device’s lifecycle. This includes cybersecurity risks, which are becoming more critical as devices connect to networks.
Cybersecurity issues like data breaches or unauthorized access can impact patient safety. For example, a cyberattack could disrupt therapy or compromise sensitive information. ISO 14971 helps manufacturers identify these risks, evaluate how likely they are, and plan how to reduce them.
Documentation is key. You need to show how you’ve addressed risks with clear plans, actions, and testing results. This connects closely to IEC 62304, which focuses on secure software development.
The FDA’s guidelines focus on ensuring medical device cybersecurity to protect patient safety. It applies to both premarket and postmarket phases, emphasizing proactive risk management.
In the premarket phase, manufacturers must design with security in mind. This includes identifying threats, addressing vulnerabilities, and documenting risk assessments and security controls.
For the postmarket phase, ongoing monitoring and timely updates are essential. The FDA encourages prioritizing actions based on the impact and likelihood of threats, ensuring devices stay secure. Transparency is also key here. Sharing information about vulnerabilities and updates helps users maintain device security.
 FDA Guidance in the light of Cybersecurity
FDA Guidance in the light of Cybersecurity
The FDA recognizes IEC 62304 as a consensus standard for software lifecycle processes in medical devices. Compliance with IEC 62304 helps manufacturers meet FDA requirements for software safety and risk management. While not mandatory, following IEC 62304 aligns with FDA guidance, ensuring robust design, development, and maintenance practices for regulatory approval.
Generally, we recommend doing IEC 62304 (along with all the cybersecurity measures) for all new projects.
International standards are key to harmonizing cybersecurity requirements. The European Union’s Medical Device Regulation (MDR) and In Vitro Diagnostic Regulation (IVDR) have strict cybersecurity guidelines for devices. The EU Cyber Resilience Act (CRA) is a broader framework for all connected devices including medical devices. This legislation requires robust security throughout the product life cycle, manufacturers must address vulnerabilities proactively and ongoing risk management.
Manufacturers must ensure their quality management systems are in line with these changing requirements to have device security across all connected devices. This global alignment, enabled by regulations like the EU Cyber Resilience Act (CRA), allows medical device cybersecurity standards to be applied uniformly and raises the overall security of the industry while protecting patient safety and trust.
From our experiences and observations of the market (probably there would be some statistics to prove this) more medical device developers decide to first go with the FDA and release the product on the American market rather than the European. In 2025 I attended the MedTech Forum in Vienna and the main topic there was how to reclaim the EU’s edge on medical devices.
Besides regulatory there is also a practice. Let’s have a look at what precisely you can do to make your device more secure.
 Medical Device Cybersecurity Pillars
Medical Device Cybersecurity Pillars
Secure medical devices start with a solid design phase. Including general requirements for device security like encryption, secure boot mechanisms and authentication protocols helps to mitigate cyber risks. The Software Bill of Materials (SBOM) gives transparency in medical device software so manufacturers can identify and address vulnerabilities in third-party components.
Software architecture is part of Scythe Studio’s offer. The foundation of secure design data encryption, strong authentication, and careful choice of connectivity protocols.
Effective security risk management is about identifying potential cyber threats and mitigating them. By doing thorough risk assessments manufacturers can prioritize security controls that protect patient data and device functionality. Organizations must also monitor the threat landscape to adapt their security strategy to new risks.
Remember that it’s not a one-shot action. You have to update the security risk assessments based on new vulnerabilities discovered in your own software and also in SOUPs.
Medical device cybersecurity is continuous. Implementing procedures for monitoring, validation, and updates ensures devices are protected throughout the product life cycle. Patch management processes must be in place to address discovered vulnerabilities quickly to protect information security and patient data.
For updates you can think about secure over-the-air (OTA) updates to fix vulnerabilities quickly and minimize downtime. Thus dissatisfaction of buyers of your devices.
Medical device manufacturers have to balance technological innovation with regulatory compliance. Cybersecurity is not just a technical issue; it affects all stakeholders in the medical device industry, patients, healthcare providers, and government agencies. Protecting medical devices from cyber risks ensures safety, trust in healthcare systems, and no legal consequences.
Connected devices are more vulnerable to cyber attacks as they are entry points for attackers. Integrating cybersecurity into every stage of the device development – from design to post-market monitoring – is key. Compliance with FDA and other international standards gives a competitive advantage, manufacturers can meet the expectations of regulators and end customers.
Remember that the cybersecurity threats are not a joke and the main goal here is not just to fulfill legal requirements, get FDA approval,l and make regulatory bodies happy. Just like software issues might lead to serious injury, cyber-attacks can cause serious damage to even a large group of people.
Let's face it? It is a challenge to get top Qt QML developers on board. Help yourself and start the collaboration with Scythe Studio - real experts in Qt C++ framework.
Discover our capabilities
Hey, welcome back to another blog post. Today we’re going to talk about the new Qt WebAssembly. This post will […]

Users of embedded devices – from industrial controllers to consumer electronics – are often unaware of hidden vulnerabilities that threaten […]

Graphical user interfaces (GUIs) are becoming more and more important in embedded devices – from home appliances to medical equipment […]