Verification and Validation Testing for Medical Devices
Verification and Validation (V&V) are two pillars that ensure a medical device is safe, effective, and compliant before it ever […]
Join us at Qt C++ Warsaw Meetup - 21.08.2025
Sign up for free!
Users of embedded devices – from industrial controllers to consumer electronics – are often unaware of hidden vulnerabilities that threaten device security across various industries. Within the medical-device sector, this threat isn’t science fiction – it’s a serious issue that has already prompted regulatory recalls. In 2017, the FDA even recalled nearly half a million pacemakers.
In this article, we’ll explore why firmware security matters so deeply, what Secure Boot really means, and how robust firmware protection can save your product from disaster. As an experienced embedded systems development team, we help solve these problems and implement security measures that actually work.
Let’s chart the path to security, step by step.
You pour heart and resources into an embedded product – be it a smart sensor, a medical device, or an automotive controller. Everything works great, until one day it doesn’t. Perhaps a hacker injected compromised firmware, bypassing protections meant for protecting embedded systems. Maybe someone tampered with an update or modified the software on the production line. The device might start acting erratically, or worse, become a puppet in a larger attack (like being recruited into a botnet of hacked IoT gadgets).
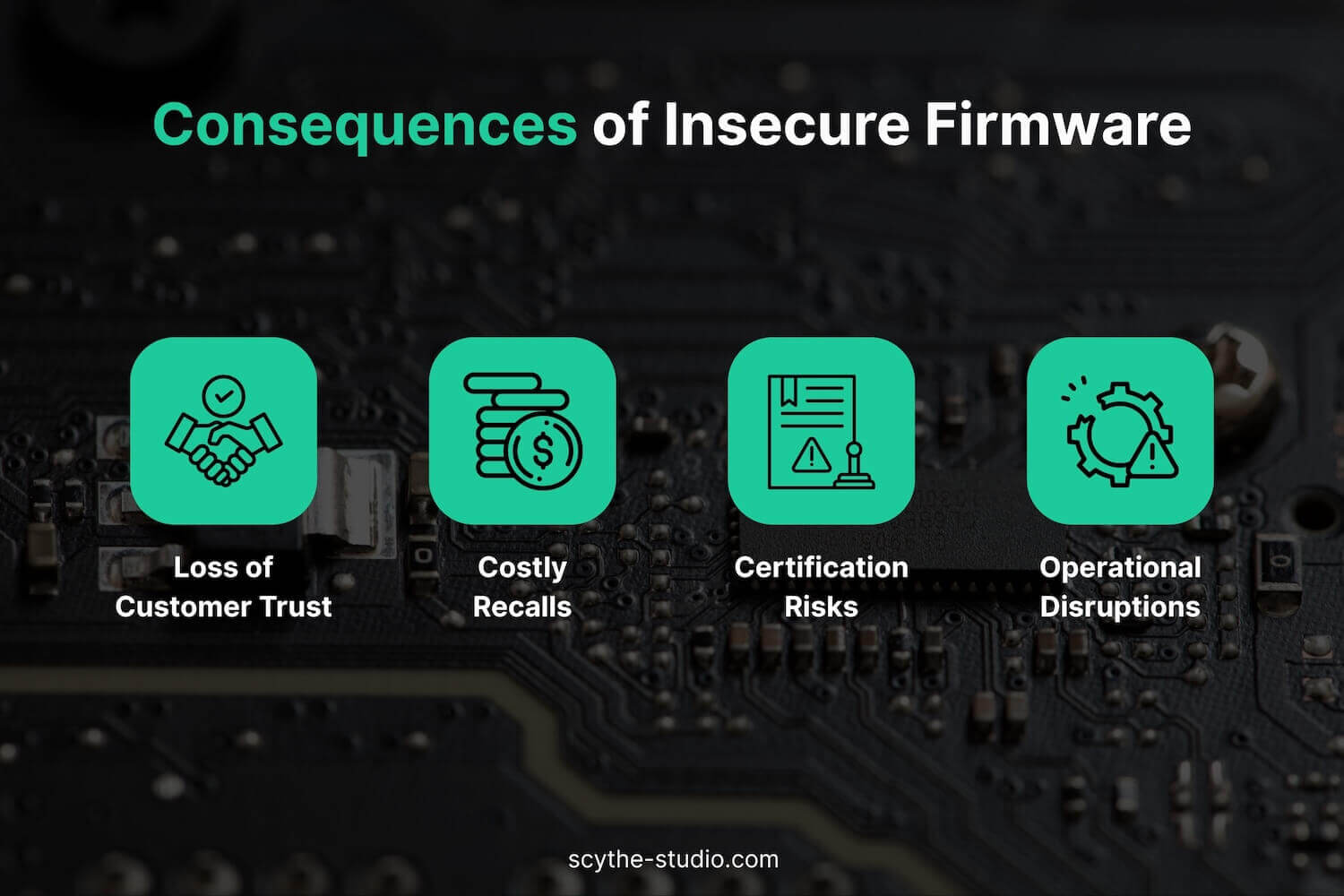
The consequences hit hard and fast when a device’s firmware is compromised:
Reading this, it’s easy to feel a knot in your stomach. These are the nightmares that keep decision-makers awake at 3 AM, wondering “Have we done enough to protect our firmware?” The harsh truth is that firmware is a prime target nowadays. Attackers have realized that going for the low-level software can be even more rewarding than hacking an app. If they control the firmware, they control the device completely.
But take a deep breath – this story doesn’t have to end in tragedy. There is a cause-and-effect relationship here that we can leverage: when you secure your firmware from the ground up, you break the attacker’s path and protect everything built on top of it. It all starts at boot time, with a concept called Secure Boot.
Think of the boot process of an embedded device as a drawbridge to a castle. Secure Boot is the guard at that drawbridge, checking every entrant’s credentials before letting them in. In more technical terms, Secure Boot ensures that when your device powers on, it only runs firmware that you have approved and trusted. If some malicious or modified code tries to start, Secure Boot slams the gate shut. No entry for bad guys.
How does Secure Boot achieve this? In simple language, it uses a digital signature based on a private key and a public key stored on the device, which are like unforgeable ID cards for software. When you, the device maker, prepare a firmware (or an update), you sign it with a secret key that only you have. Inside the device, during boot-up, a tiny piece of immutable code (often in one time programmable memory) holds the public key corresponding to your secret. The device uses this to verify the signature on the firmware trying to load. If the signatures don’t match or the code was altered, the verification fails – so the device refuses to run that code. This guarantees the integrity and authenticity of the code before the device boots. In effect, if it’s not you, it doesn’t boot.
Secure Boot establishes a Root of Trust at the very start of execution. It’s like laying a foundation stone that the rest of the house builds on. Because each stage of the boot process checks the next one, a chain of trust forms. The bootloader checks the kernel, the kernel can check application code, and so on. Each link in the chain must be intact, or the chain breaks and everything stops. This might sound harsh (the device not booting), but it’s far better than booting into compromised code that silently causes harm. A device that refuses to start when tampered is far preferable to one that starts and does the wrong thing.
Of course, implementing Secure Boot isn’t as simple as flicking a switch. It requires hardware support (the device needs a place to securely store keys and an unalterable boot code segment) and careful setup of keys and signatures. But when done right, it establishes a trusted foundation for the system, enabling additional layers of security to protect it throughout its operation, not just during the boot process.
To see Secure Boot in action, consider a simplified scenario in a medical infusion pump device:
If at any point a verification fails, the device should refuse to proceed. It might blink an error LED, reset, or enter a fail-safe mode (perhaps reverting to a known-good backup firmware if available).
While the benefits of Secure Boot are clear, implementing it in embedded systems – especially resource-constrained or legacy ones – comes with challenges. Decision-makers should be aware that Secure Boot is not a flip-a-switch software feature; it’s a complex process that requires careful design, the right hardware support, and ongoing management. Here are some common challenges:
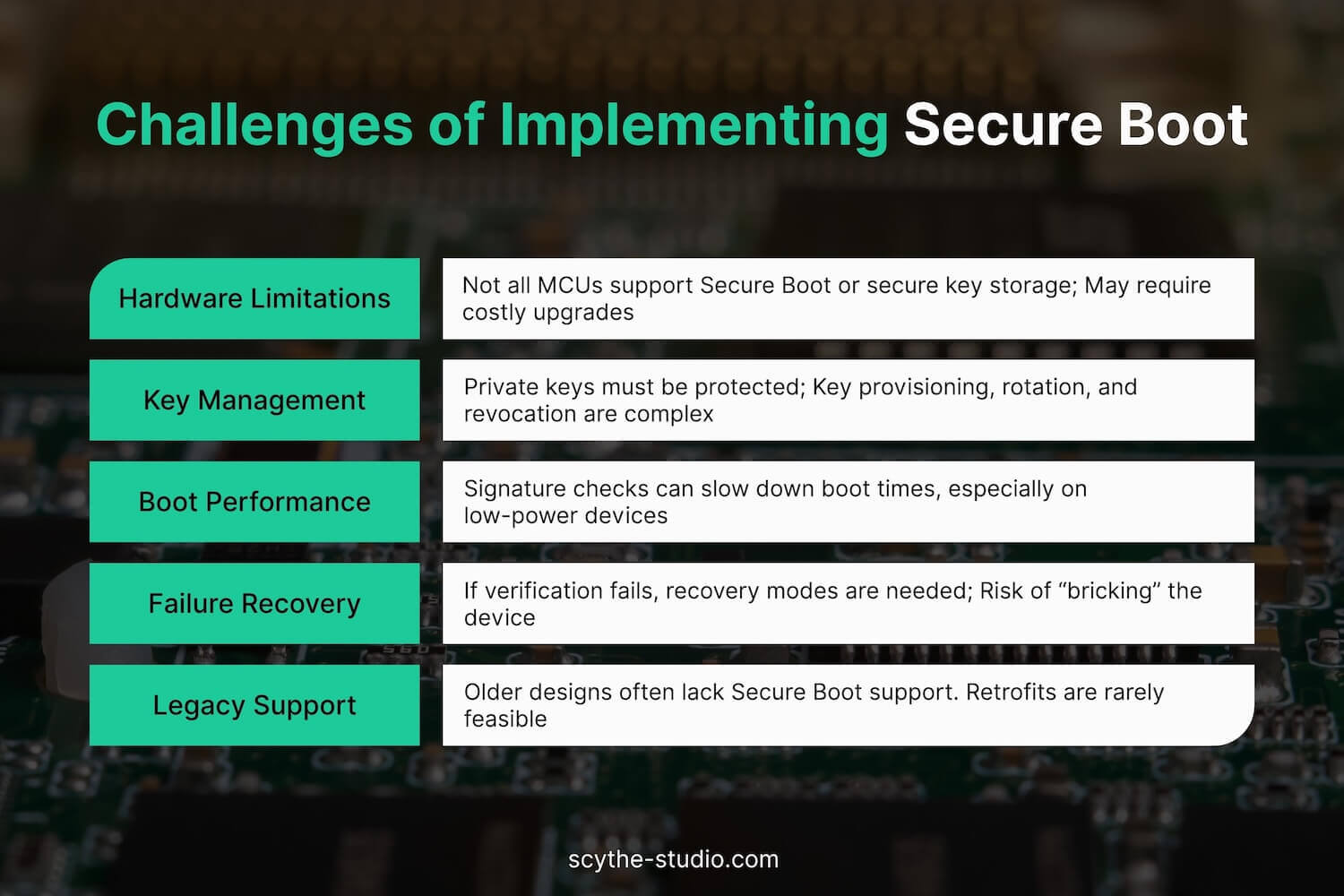
Not all microcontrollers or SoCs support Secure Boot making it difficult to enable Secure Boot on resource-limited platforms. Many basic MCUs just boot whatever is in flash. In such cases, engineers must implement their own secure bootloader, which adds complexity and requires deep hardware knowledge. Lack of crypto accelerators or dedicated hardware security modules like trusted platform modules (TPMs) can slow down boot time, and secure key storage is often missing in low-cost parts. Sometimes, switching to a more capable chip is necessary—impacting cost, power, and effort.
Secure Boot depends on proper key handling. The private signing key must be tightly protected, and the public key must be securely provisioned into each device during manufacturing. Supporting key updates or revocation adds complexity but is critical for long-lived devices. It also requires managing different key lengths and ensuring that update tools respect proper firmware update mechanisms. Mistakes here can compromise all devices in the field.
Signature checks take time and resources. On low-power devices, verifying large images may delay startup. While modern hardware and ECC help reduce this, the added latency still needs to be considered—especially for real-time systems. Optimization and staged verification can help.
If a Secure Boot check fails, the device must fail safely—e.g., booting a backup image or entering recovery mode. This requires extra flash and careful update logic. Without it, a bad update could brick the device, which is unacceptable in critical systems like medical devices.
Implementing Secure Boot correctly is hard. It touches hardware, cryptography, manufacturing, and software security. Many teams lack the required expertise, and even large vendors have made mistakes. It’s common to rely on external specialists or proven frameworks.
&nbs
Adding Secure Boot to existing products is usually not possible without hardware support. New designs must plan for it from the start. Debug or maintenance modes must also be locked down to prevent bypasses in production.
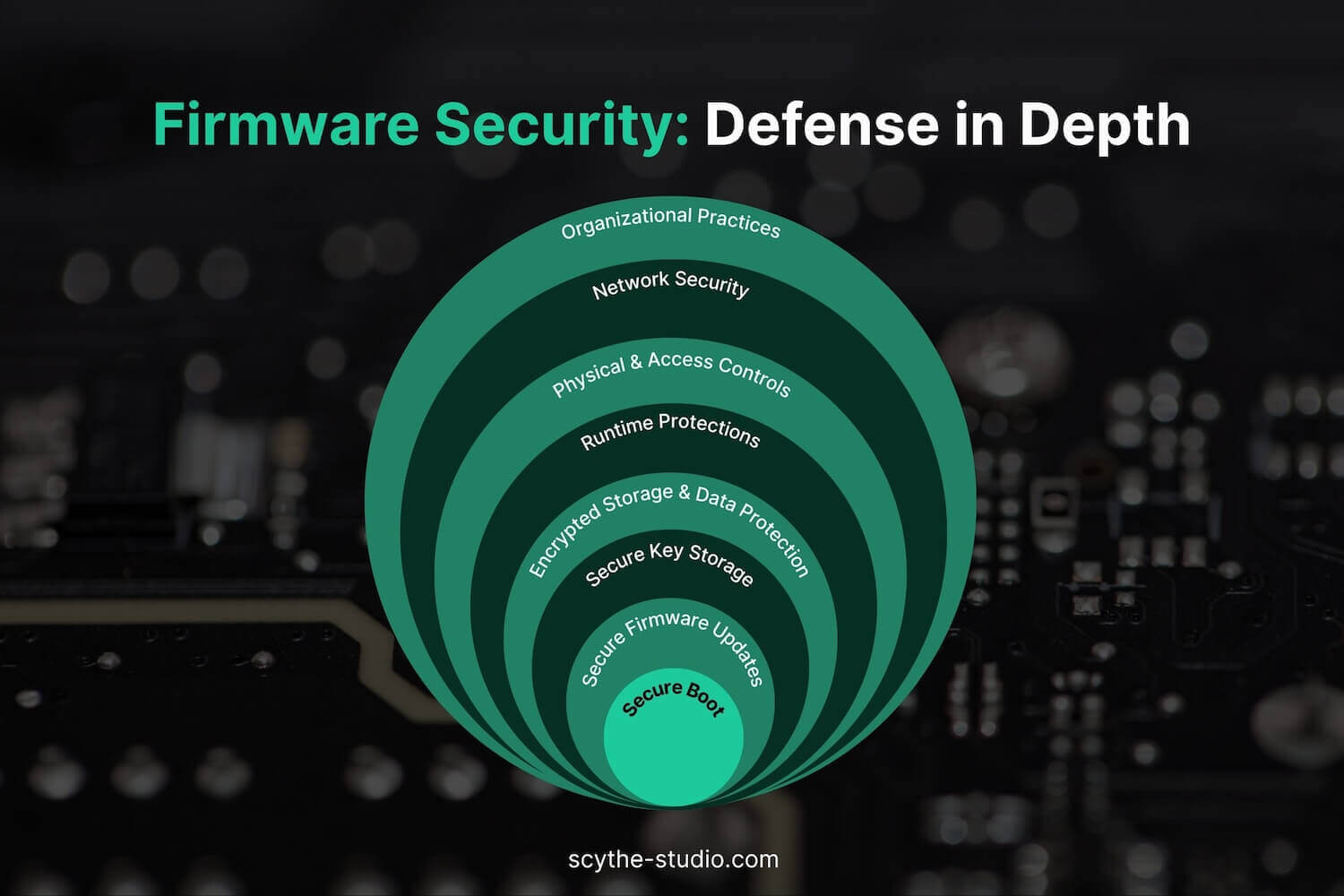
While Secure Boot is a cornerstone of firmware protection, it should be combined with other security measures to achieve a robust defense-in-depth. Think of it like layers of an onion – an attacker should have to peel through multiple safeguards, and breaching one layer still leaves others in place to protect the system. Here are key layers that complement Secure Boot in embedded systems:
WhileSecure Boot is only effective if firmware updates are also verified. Updates must be digitally signed, ideally using the same keys as the initial firmware. OTA and media-based updates should enforce signature checks to block tampered code. Encryption adds confidentiality, but authenticity is the priority. Include rollback protection to prevent downgrading to vulnerable versions. Also consider securing remote firmware updates, especially for field-deployed systems.
WhileModern MCUs often provide secure boot features and isolated storage for cryptographic keys (e.g., TrustZone, TPMs, secure elements). Leveraging these reduces the risk of key exposure and makes bypassing Secure Boot physically difficult. Hardware-based roots of trust provide stronger assurance, especially in safety-critical applications. These can serve as an extra layer of protection, isolating encryption keys from software access.
WhileIf the device stores sensitive data (e.g., patient info or proprietary configs), encrypt it. Secure Boot can tie into this by unlocking keys only after verifying firmware. This ensures attackers can’t access or tamper with data, even if they gain memory access.
After boot, the device still needs runtime defenses:
These defenses are critical for enhancing security after the secure boot process ends.
WhileDisable debug interfaces (e.g. JTAG), enable flash readout protection, and physically secure the device. Use tamper seals or sensors in high-security products. Eliminate factory-default credentials and lock down service modes before deployment.
WhileDevices with connectivity must authenticate remote commands and encrypt communications (e.g., TLS). Use mutual authentication to prevent spoofing or MITM attacks. Secure boot is only one part—network controls are critical too.
WhileAdopt secure development processes (e.g., IEC 62304 with threat modeling, secure coding, and fuzz testing). Plan for vulnerability response with coordinated disclosure and timely patches. Security is not just technical—it’s also procedural.
For decision-makers, implementing this multi-layer security may sound daunting, but resources exist – from reference designs by silicon vendors to consulting firms specializing in embedded security. The key takeaway is no single technique is a silver bullet. Secure Boot is a big piece of the puzzle (arguably the most important for integrity).
When the pressure is on to secure your embedded device, teaming up with the right people can make all the difference. A true expert partner brings something invaluable to the table: hard-earned experience across all facets of embedded systems development, plus a razor-sharp focus on security. Here’s why that matters and how it directly addresses the pain points we discussed:
Secure boot and firmware protection are essential pillars of embedded system security in defending devices against cyber attacks and maintaining trusted firmware operations. By ensuring that an embedded device only executes authenticated, untampered code from the moment it boots, these techniques create a foundation of trust that shields devices from unauthorized control and exploitation. Mechanisms such as cryptographic signatures, hardware roots of trust, and chained firmware validation work together to defend against both remote attackers and hands-on hardware hackers. The result is a more resilient device – one that preserves the integrity of its operations, protects sensitive data and intellectual property, and maintains the confidence of users and stakeholders.
For companies developing or deploying embedded systems, investing in secure boot and firmware protection is a prudent decision. Not only do these measures reduce the risk of cyberattacks and costly vulnerabilities, but they also signal a commitment to quality and security that can differentiate your products in the marketplace. Implementing secure boot does introduce complexity – keys must be managed, manufacturing processes must accommodate device personalization, and developers must adhere to signing and update protocols – but these are manageable with the right expertise. This is why organizations often seek out embedded security professionals or consultants when embarking on such projects. Having experts who understand embedded cryptography, hardware trust anchors, and secure update processes is invaluable to getting it right.
Let's face it? It is a challenge to get top Qt QML developers on board. Help yourself and start the collaboration with Scythe Studio - real experts in Qt C++ framework.
Discover our capabilities
Verification and Validation (V&V) are two pillars that ensure a medical device is safe, effective, and compliant before it ever […]

From medical devices and smart vehicles to industrial controllers and consumer electronics, embedded systems are everywhere—and increasingly connected. But with […]
Hey, welcome back to another blog post. Today we’re going to talk about the new Qt WebAssembly. This post will […]