How to use Qt WebAssembly – The Complete Guide with demo
Hey, welcome back to another blog post. Today we’re going to talk about the new Qt WebAssembly. This post will […]
Join us at Qt C++ Warsaw Meetup - 21.08.2025
Sign up for free!
From medical devices and smart vehicles to industrial controllers and consumer electronics, embedded systems are everywhere—and increasingly connected. But with connectivity comes vulnerability. A single security flaw can open the door to data breaches, safety incidents, large-scale disruptions, or even regulatory fines. These embedded computers often control critical functions such as braking, drug delivery, or access to private data—functions where compromise could lead to real-world harm. Given this, understanding embedded security is no longer optional.
In this article, you’ll learn:
At Scythe Studio, we specialize in designing and developing secure software for embedded systems.
If you’re developing an embedded product, now is the time to get security right. Let’s talk about how we can help.
Embedded system security is the practice of protecting embedded devices and their software from unauthorized access, misuse, and attack. In other words, it focuses on preventing malicious parties from accessing or controlling the specialized computers hidden inside products ranging from industrial controllers to home appliances. This field covers both software and hardware security measures.
Embedded systems face a wide array of cyber threats and attack vectors. An attack vector is the path or means by which an attacker can gain unauthorized access to a device. Below we outline the main categories of threats, including firmware/software attacks, communication exploits, physical attacks, and supply chain risks, along with examples of each:
One major category involves attacks on the firmware or software running on the embedded device. Because embedded software is often coded in low-level languages (C/C++) and runs on constrained hardware, it may contain memory-management bugs or weak protections similar to early computing systems. Common software-based attacks include:
These vulnerabilities are particularly concerning when they exist in embedded operating systems or in widely reused software components, as exploitation at that level can cascade across many devices sharing the same codebase.
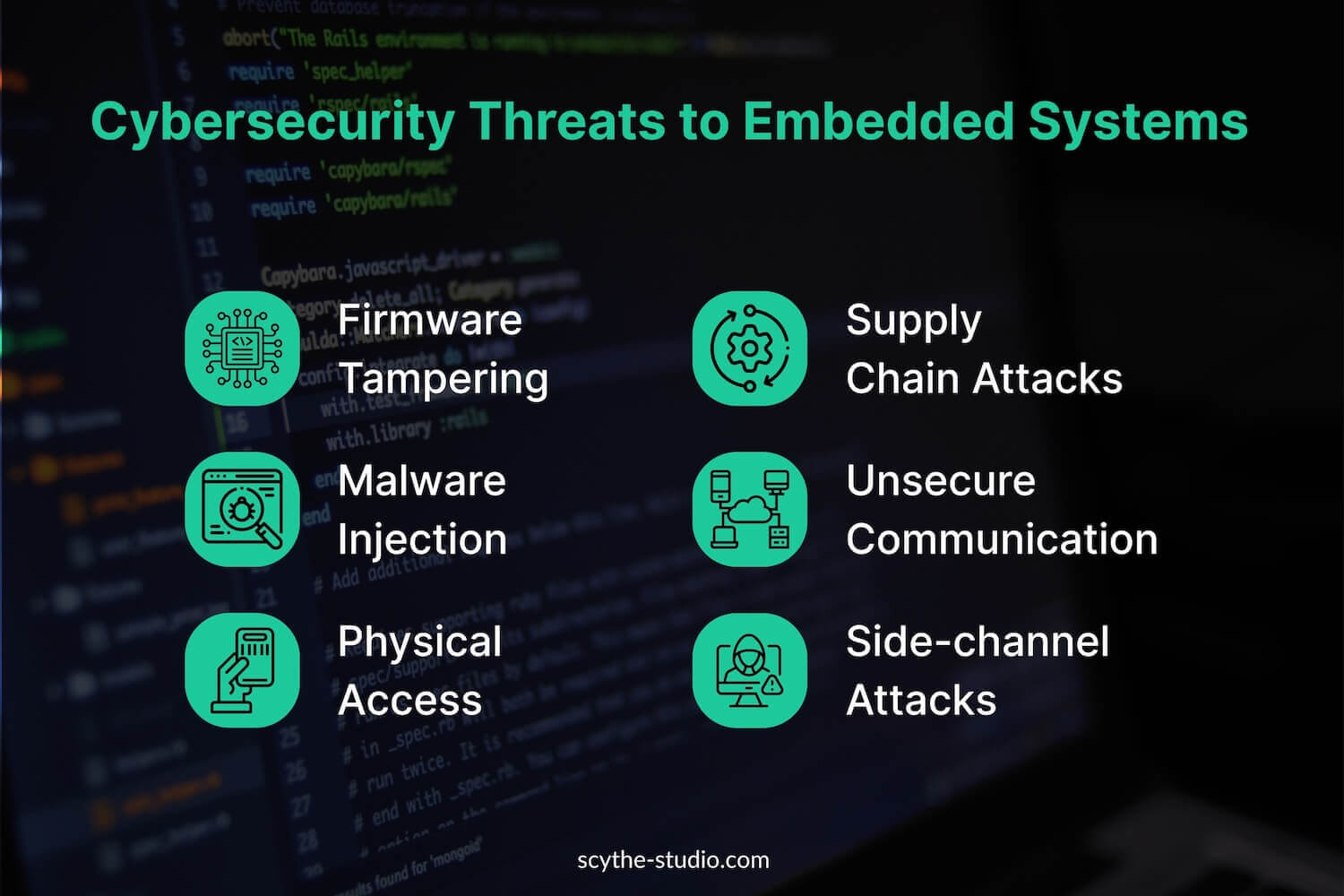
Successful software/firmware attacks can give adversaries control over the device or access to sensitive data. For instance, malware can spy on or sabotage the device’s function, while a buffer overflow exploit might drop the attacker into a root shell. Because these attacks often can be done remotely (over a network or radio connection), they are especially dangerous – a hacker might compromise thousands of devices across the internet if they share the same software flaw.
Even more concerning, many of these attacks can succeed against only software protections if there is no hardware-backed enforcement, making layered security critical.
Communication protocols in embedded systems play a crucial role in enabling data exchange between devices and systems. These protocols—such as Wi-Fi, Bluetooth, CAN bus in cars, and industrial Ethernet—are often the target of attacks, as adversaries attempt to intercept, manipulate, or disrupt the transmitted data:
Network-based exploits can allow attackers to monitor sensitive data in transit or hijack control of devices from afar. For instance, an attacker on the same Wi-Fi network might sniff and steal credentials sent by a medical device, or send malicious commands to an industrial controller to disrupt a process. Ensuring secure communication (encryption and authentication) is therefore a cornerstone of embedded cybersecurity.
Organizations need to consider the potential security risks of exposing devices to unencrypted wireless interfaces and weak protocol implementations, especially when designing a connected device expected to run autonomously in the field.
Unlike enterprise servers locked in data centers, embedded systems are often deployed in uncontrolled, public, or easily accessible environments. This opens them to physical tampering and low-level hardware attacks:
Hardware attacks are often more difficult and costly for the attacker (requiring physical presence and specialized skills) but can be devastating when pulled off. They can bypass upper-layer security entirely – for example, extracting a cryptographic root key from a device via side-channel means the attacker can then decrypt all communications or impersonate the device at will. Many hardware vulnerabilities are also unpatchable or hard to fix without a new hardware revision (you can’t “update” a circuit the way you patch software). Thus, devices must be designed with physical security in mind – using techniques like tamper-resistant casings, sensors that zeroize keys if opened, disabling or locking debug ports, and using secure hardware elements for key storage.
Unlike network threats, these attacks directly target the physical device and often aim to bypass protections implemented in hardware components such as secure bootloaders or key storage modules.
Another critical vector for embedded systems is the supply chain – both the supply chain of components during manufacturing and the software update chain during the product’s life. Attackers may target weaknesses before the device even reaches the end user:
Supply chain attacks can potentially compromise many devices at once (e.g., if a backdoor is built into a widely used component or a popular update server is hacked). These attacks are harder for individual end-users to detect or defend against, since they occur upstream.
Security also depends heavily on trusted third party components—even a small vulnerability in a vendor-supplied library or chip can severely affect security downstream, making vendor risk management part of cybersecurity strategy.
Embedded systems are exposed to both software and hardware vulnerabilities, each with distinct characteristics, attack methods, and mitigation challenges. Software flaws are typically more numerous and can often be patched via updates, whereas hardware flaws are harder to fix once deployed and may require physical changes or product recalls.
The table below summarizes key differences:
| Aspect | Software Vulnerabilities | Hardware Vulnerabilities |
|---|---|---|
| Nature | Bugs in code logic, input handling, or configuration (e.g., buffer overflows, auth flaws). | >Design flaws in components or physical interfaces (e.g., exposed debug ports, weak RNGs). |
| Exploitation Method | Remote attacks via network packets, interfaces, or default credentials. | Requires physical access or specialized tools (e.g., glitching, side-channel attacks). |
| Detection Visibility | May trigger logs, crashes, or anomalies detectable via software monitoring. | Often stealthy; no logs generated, only physical or electrical side-effects observable. |
| Fixability | Can usually be mitigated with firmware/software updates. | Typically unpatchable; may require hardware revision or physical countermeasures. |
| Persistence | Easier to fix over time with proper update mechanisms. | Persist across all affected units unless physically addressed. |
| Lifecycle Impact | Vulnerabilities emerge as software ages or support ends. | Remain inherent in device hardware over its entire operational lifespan. |
Proper isolation of trusted functions in hardware and the use of secure key storage can mitigate risks that are otherwise unmanageable with software alone.
The cybersecurity risks and priorities for embedded systems can vary greatly by industry. A medical infusion pump, an automotive ECU, and a smart thermostat all have embedded computers, but the consequences of a breach and the threat landscape are very different. Below we discuss a few key industries – automotive, healthcare, industrial/IIoT, and consumer electronics/IoT – highlighting the unique concerns and standards of each.
| Sector | Key Cybersecurity Risks | Security Measures & Design Priorities | Relevant Regulations & Standards |
| Automotive and Transportation | Remote attacks on vehicle systems (e.g. infotainment, CAN bus); risk of loss of control, theft, privacy breaches. | Security by design; comply with ISO/SAE 21434 and UNECE WP.29; secure OTA updates; in-vehicle network segmentation; ECU authentication; threat monitoring (vehicle SOC). | UNECE WP.29 (mandatory in EU, UK, Japan); ISO/SAE 21434 (industry standard); NHTSA guidelines (US); cybersecurity part of type approval. |
| Healthcare and Medical Devices | Wireless manipulation of implants (pacemakers, insulin pumps), hospital device tampering (e.g. infusion pumps), ransomware attacks. | Encryption/authentication for device communication; segmenting medical networks; security lifecycle management per IEC 62304; patching capabilities; fail-safe mechanisms. | FDA premarket cybersecurity requirements (US); EU MDR (Europe); IEC 62304, ISO 14971, AAMI TIR57, UL 2900 (standards); FD&C Act amendments (2023). |
| Industrial IoT and Critical Infrastructure | Targeted attacks (e.g. Stuxnet), ransomware, legacy protocols lacking authentication, IT-OT network crossover. Risks include physical damage and service disruption. | Defense-in-depth with IEC 62443; network segmentation (zones and conduits); strong access control; secure configurations; OT monitoring; patching during maintenance windows. | NERC CIP (US energy sector); IEC 62443 series (widely adopted); EU NIS 2 directive (2023); national frameworks (e.g., Germany’s BSI ICS Security Compendium). |
| Consumer Electronics and IoT | Default credentials, lack of updates, privacy issues (spying), botnets (e.g. Mirai), lateral attacks within home networks via vulnerable IoT devices. | Unique credentials; secure onboarding; OTA updates; encrypted data at rest/in transit; user transparency; security features on by default. | EU Cyber Resilience Act (CRA, 2024); ETSI EN 303 645; California SB-327 (US); UK PSTI Act (2022); voluntary labels (e.g., Singapore’s IoT labeling scheme). |
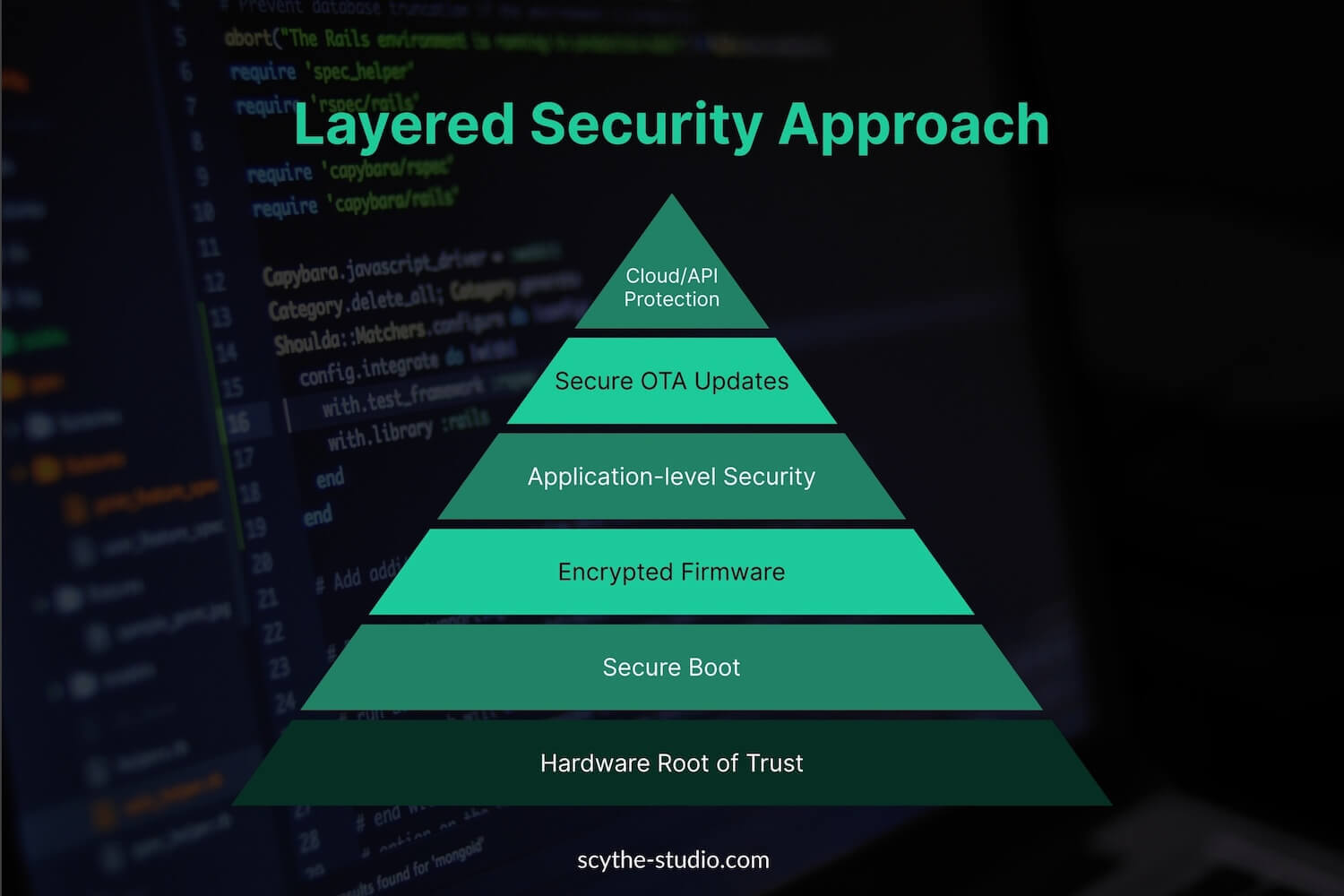
Securing embedded systems requires a multi-layered approach, addressing everything from the hardware up through software, and even the processes by which the device is developed and maintained. Below are key countermeasures and best practices, which together form a defense-in-depth strategy for embedded cybersecurity:
One of the most foundational security mechanisms is implementing secure boot, which ensures the device runs only verified firmware during startup. Secure boot mechanisms use cryptographic signatures to verify firmware integrity at each stage of boot-up. The device contains a hardware or ROM-based root of trust (e.g., a public key burned into the silicon) that is used to validate the bootloader, which in turn validates the next layer (OS kernel), and so on. If any code has been tampered with or is not signed by the device manufacturer, the boot process halts, preventing untrusted code from running. Secure boot should also be complemented by measured boot or attestation where possible (recording cryptographic hashes of boot components that can be remotely verified).
Leverage dedicated security hardware available in modern chips. Many embedded processors now offer features like Trusted Execution Environments (TEE) (e.g., ARM TrustZone) which isolate sensitive code into secure regions that normal code cannot access. Utilizing these can protect critical operations (crypto, authentication routines) even if the main application is compromised. Similarly, a Trusted Platform Module (TPM) or secure element chip can store cryptographic keys securely and perform sensitive operations (encryption, signing) in isolation. Best practice is to store private keys, device identity certificates, and other credentials in secure hardware so that a hacker who compromises the application code still cannot extract these secrets. Additionally, many chips now offer a hardware root of trust, enabling strong identity and chain-of-trust validation from the moment power is applied.
The choice and implementation of encryption algorithms must align with modern cryptographic standards. These help protect sensitive data, prevent data theft, and preserve privacy even if communications are intercepted. Each device ideally has a unique identity (keys/certificates) to facilitate mutual authentication with back-end services or other devices. For data at rest (stored on the device’s flash or disk), full-disk encryption (FDE) is highly recommended, especially if the device carries any private data or credentials.
Embedded devices should ship in a “hardened” state with unnecessary features removed or disabled. Best practices include: turning off debug interfaces in production, removing test or demo code, using firewall rules to restrict network access, and disabling default login accounts. Applying the principle of least privilege is important – for example, if the device has multiple processes, they should run with minimal privileges and be isolated (via process isolation, containers, or a microkernel architecture) so a compromise in one doesn’t immediately compromise all. Many embedded Linux systems now utilize technologies like SELinux or AppArmor to enforce policy constraints on what each process can do.
Additionally, secure default settings should be used: require users to set strong passwords, use secure communication by default (no fallback to plaintext), and ship with secure configurations out-of-the-box. Hardening also means protecting memory and interfaces: for instance, enabling hardware MPU/MMU features to prevent execution in writable memory (NX bit) and using stack canaries and ASLR to make exploits harder. Though resource constraints exist, many of these protections have minimal performance impact and significantly raise the bar for attackers. Hardening steps may also include disabling bootloader unlocks, enforcing secure storage of secrets, and isolating critical systems with microkernel designs or containers.
No matter how much testing is done, some vulnerabilities will eventually be discovered after deployment. Thus, having a robust firmware update mechanism is vital. Firmware must be signed and authenticated, and the update channel should be protected with transport-level data encryption. A software bill should track all components used in each firmware version for easier patching and audits.. Manufacturers should have a plan for how long they will provide updates (and communicate this to customers). Automated update delivery is ideal for consumer devices (to ensure patches actually get applied), whereas industrial or medical updates might require scheduling to avoid downtime – but the capability needs to be there. A failsafe mechanism is also recommended: for example, dual firmware slots so that if a new update fails, the device can revert to the last known good state (preventing “bricking” in case an update is interrupted).
Security should be woven into every stage of the embedded systems development. Developers should follow secure coding practices and apply early risk assessment to address vulnerabilities before they are embedded in the firmware. A formalized SDLC should include security testing stages at every phase of software development. This means conducting threat modeling early on to foresee potential attacker goals and entry points, then designing controls to mitigate those. During implementation, developers should follow secure coding guidelines (e.g., MISRA C for safety/security, or CERT C coding standards to avoid common pitfalls). Use of memory-safe languages for critical components can also reduce certain bug classes. Static analysis (SAST) tools can catch buffer overruns, unsafe functions, and other issues in source code. Dynamic testing and fuzzing should be applied to device interfaces. Penetration testing (ethical hacking) on the device and its ecosystem (mobile apps, cloud endpoints) is highly recommended.
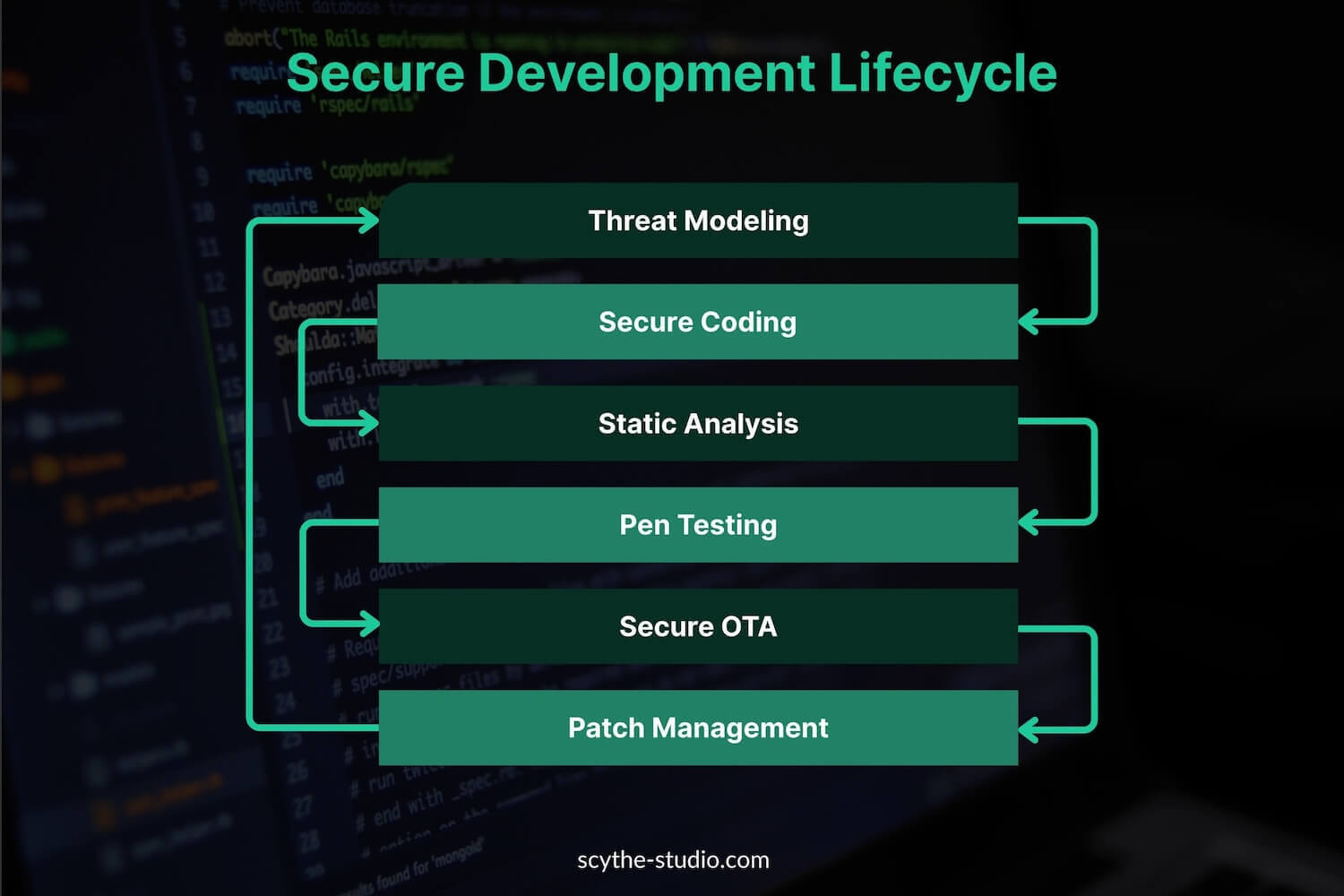
It’s wise to assume that no system is 100% hack-proof. Thus, implementing mechanisms to detect and respond to intrusions can mitigate damage. Manufacturers and users should have an incident response plan: e.g., the ability to quarantine a compromised device (network isolation), analyze forensic data (if available), and recover (which might involve re-flashing firmware or, worst-case, physical replacement). It’s also crucial to allocate enough processing power and memory to support lightweight monitoring agents, especially on constrained devices. This allows real-time detection of network attacks or other anomalies.
Lastly, organizations building embedded systems should document their security requirements, design decisions, and test results. This not only helps in compliance with standards, but ensures continuity (so that if a new team picks up the product maintenance, they understand the security architecture). Comprehensive documentation should also align with embedded systems security standards, ensuring traceability and auditability throughout the five distinct security lifecycle phases. Investing in training for embedded developers can drastically reduce future vulnerabilities. Providing security training for developers, and even for end-users (to the extent users interact with the security features), can greatly improve the overall posture.
Cybersecurity for embedded systems is a multi-faceted challenge, but it boils down to a simple principle: protect the device as a whole system, considering all ways an attacker might try to compromise it. By understanding the threat landscape – from software bugs and network exploits to physical attacks – and by applying defense-in-depth measures, companies can significantly reduce the risk of breaches. The appropriate balance of measures may differ by industry (a pacemaker will prioritize safety and reliability, while a consumer gadget might focus on privacy and resilience against botnets), but the core tenets of secure design apply everywhere.
At Scythe Studio, we build secure, connected products from the ground up. If you’re working on an embedded system, now is the time to make cybersecurity a first-class design priority. Whether you’re in automotive, healthcare, industrial IoT, or consumer electronics—we can help you architect for security, meet regulatory requirements, and avoid costly mistakes.
Let’s talk about how to make your product not just functional, but resilient.
Let's face it? It is a challenge to get top Qt QML developers on board. Help yourself and start the collaboration with Scythe Studio - real experts in Qt C++ framework.
Discover our capabilities
Hey, welcome back to another blog post. Today we’re going to talk about the new Qt WebAssembly. This post will […]

Users of embedded devices – from industrial controllers to consumer electronics – are often unaware of hidden vulnerabilities that threaten […]

Graphical user interfaces (GUIs) are becoming more and more important in embedded devices – from home appliances to medical equipment […]