
Cybersecurity for Embedded Systems
From medical devices and smart vehicles to industrial controllers and consumer electronics, embedded systems are everywhere—and increasingly connected. But with […]
Join us at Qt C++ Warsaw Meetup - 21.08.2025
Sign up for free!
As devices handle more sensitive data, security has become a top priority in embedded deployments. Embedded systems – from IoT sensors and medical devices to industrial controllers and automotive components – are deployed in the field, outside the protection of the data center. They can be lost, stolen or tampered with and confidential information exposed. Full disk encryption (FDE) has become the answer to protect data at rest on these devices. By converting stored data into unreadable code, FDE ensures only authorized parties can access the data.
At Scythe Studio, we develop embedded systems and we know the growing need for strong data protection on connected devices. In this article we will explore how embedded full disk encryption strengthens device security, the risks it mitigates and the value it brings to the end user. We’ll focus on the business and security benefits, explained in a way that’s understandable to decision makers, with just enough technical detail to show how it works in practice.
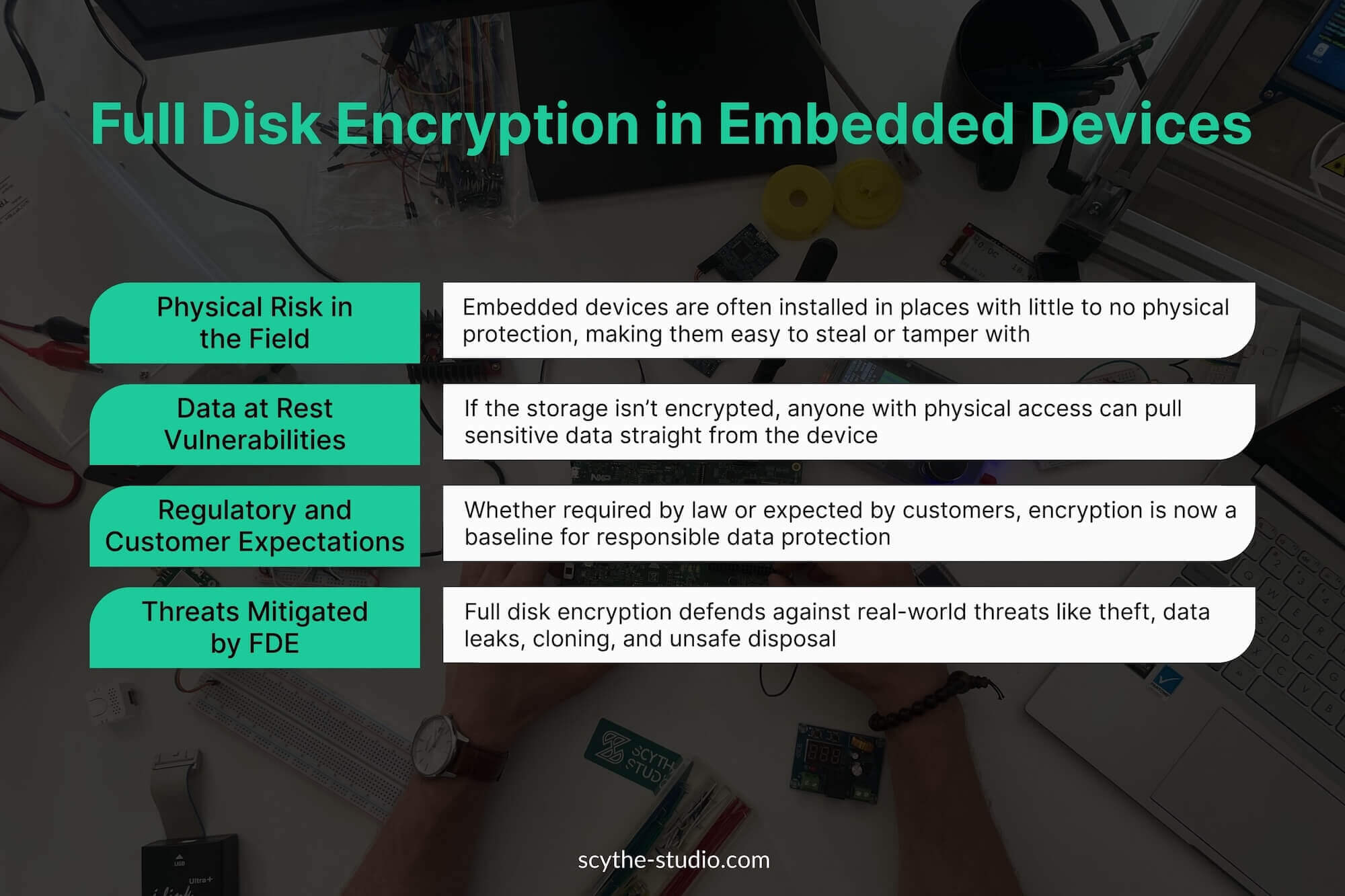
Embedded devices operate in environments where physical access controls are weak or non-existent. Unlike servers in data centers, devices in the field (smart meters, remote sensors, handheld terminals) are deployed in “unsecure environments” – anywhere people can get their hands on them. This is a big risk: if an attacker or unauthorized person gets the device, they can read data from its storage or extract its memory chips. In fact, studies show a significant percentage of data breaches come from lost or stolen devices. A misplaced embedded device with customer data or cryptographic keys could be part of that statistic if not properly protected.
Data stored on an embedded device (data at rest, or device-side data storage) is vulnerable when an attacker has physical possession of the device. For example, consider an patients vital parameters monitor that records personal medical information, or an industrial controller logging operational data. If someone pulls the storage from such a device, they might retrieve sensitive records, system credentials or proprietary software.
A famous case highlighting this kind of risk involved discarded digital photocopiers; investigators recovered thousands of sensitive documents from copier hard drives that hadn’t been encrypted. This shows that lack of encryption on storage media can turn even ordinary equipment into “gold mines” of private information for anyone with basic technical skills. Embedded products, from medical devices to ATMs, face similar risks if their storage is left unencrypted.
In many industries, protecting data at rest isn’t just good practice – it’s a compliance requirement. Regulations like HIPAA in healthcare and PCI-DSS in finance demand that sensitive data stored on devices be adequately protected (often implying encryption). Even when not strictly mandated by law, enterprise customers and consumers are increasingly aware of privacy issues and expect device manufacturers to safeguard their data. Failing to protect data can lead to legal penalties, breach notification costs and reputational damage. For a device maker, one security incident can erode customer trust and harm business. Decision makers thus recognize that strong data protection is part of the product’s value proposition, not an optional add-on.
Full Disk Encryption (FDE) is a technology that encrypts the entire storage volume of a device so that all data is protected – effectively, “every bit of data that goes on the disk” is stored in an encoded form. Unlike file-level encryption (where specific files or folders are encrypted individually), FDE operates at the disk or block level. This means that as data is written to storage, it’s automatically encrypted on the fly, and as data is read by the system, it’s decrypted – all in real time and transparently to the user.
Note that the only part of a storage device that might not be encrypted in a full disk encryption scheme is a small bootloader area needed to start the system (often called the master boot record or MBR on PCs). In many implementations of FDE, the MBR or bootloader remains unencrypted so that it can load the software that asks for the decryption key. However, modern hardware-based encryption solutions can even encrypt the entire boot disk including such boot regions. In the context of embedded systems, there are techniques to avoid exposing even the bootloader – for example, using a secure boot ROM or storing the boot code in secure memory. In practice, the combination of secure boot and FDE ensures that all code and data on the device are protected against unauthorized access or alteration.
To illustrate, consider a simplified example: an embedded Linux device uses a technology called dm-crypt (the Linux kernel’s built-in disk encryption driver) to protect its flash storage. When the device boots, a small initial program (in an initramfs or secure enclave) prompts for a decryption key or fetches it from a secure source, then unlocks the main filesystem. From that point on, all reads and writes go through the dm-crypt layer, which uses strong encryption as part of a real-time encryption process based on the Advanced Encryption Standard (commonly AES-256) to decrypt data when reading from flash and encrypt data when writing. If an attacker removed the flash chip and tried to read it directly, they would only see encrypted bytes – utterly meaningless without the 256-bit key. Importantly, this encryption is transparent during normal use; the running system and applications are unaware of the encryption, beyond a slight processing overhead that modern CPUs or crypto engines can handle efficiently.
Whole disk encryption can be implemented via software running on the main processor or via specialized hardware in the storage device or chipset. Both achieve the same end result (encrypted data), but there are differences in performance and deployment:
This approach, called full disk encryption software, uses the device’s main CPU to encrypt/decrypt data (as with dm-crypt). It’s flexible and can be used on any storage type. However, pure software encryption uses CPU cycles, which can impact performance on resource-constrained embedded processors. The performance impact varies – if the processor includes a symmetric encryption accelerator, the overhead can be minimal, but without such support, encryption can introduce latency. Many embedded CPUs today do include AES acceleration instructions or modules, so software FDE is quite viable without noticeable slow-downs.
Here, the encryption is built into the storage device itself or an associated security chip. A common example is the Self-Encrypting Drive (SED) which implements the Trusted Computing Group’s Opal standard for drive encryption. An Opal-compliant SED (often an SSD) automatically encrypts all data that goes onto it, using an internal hardware engine. From the outside, it just looks like a normal drive, but it is always encrypting and decrypting data internally. The encryption key is stored securely in the drive’s controller hardware, and the user unlocks the drive (usually via a password or key provided at boot time) to allow it to read/write data. The advantages are excellent performance (encryption has virtually no impact on read/write speed) and ease of use – no special software stack is needed to leverage. Once unlocked, it’s completely transparent to the operating system and user. Additionally, because the keys never leave the drive, sensitive keys are isolated from the main system’s memory, reducing attack surface.
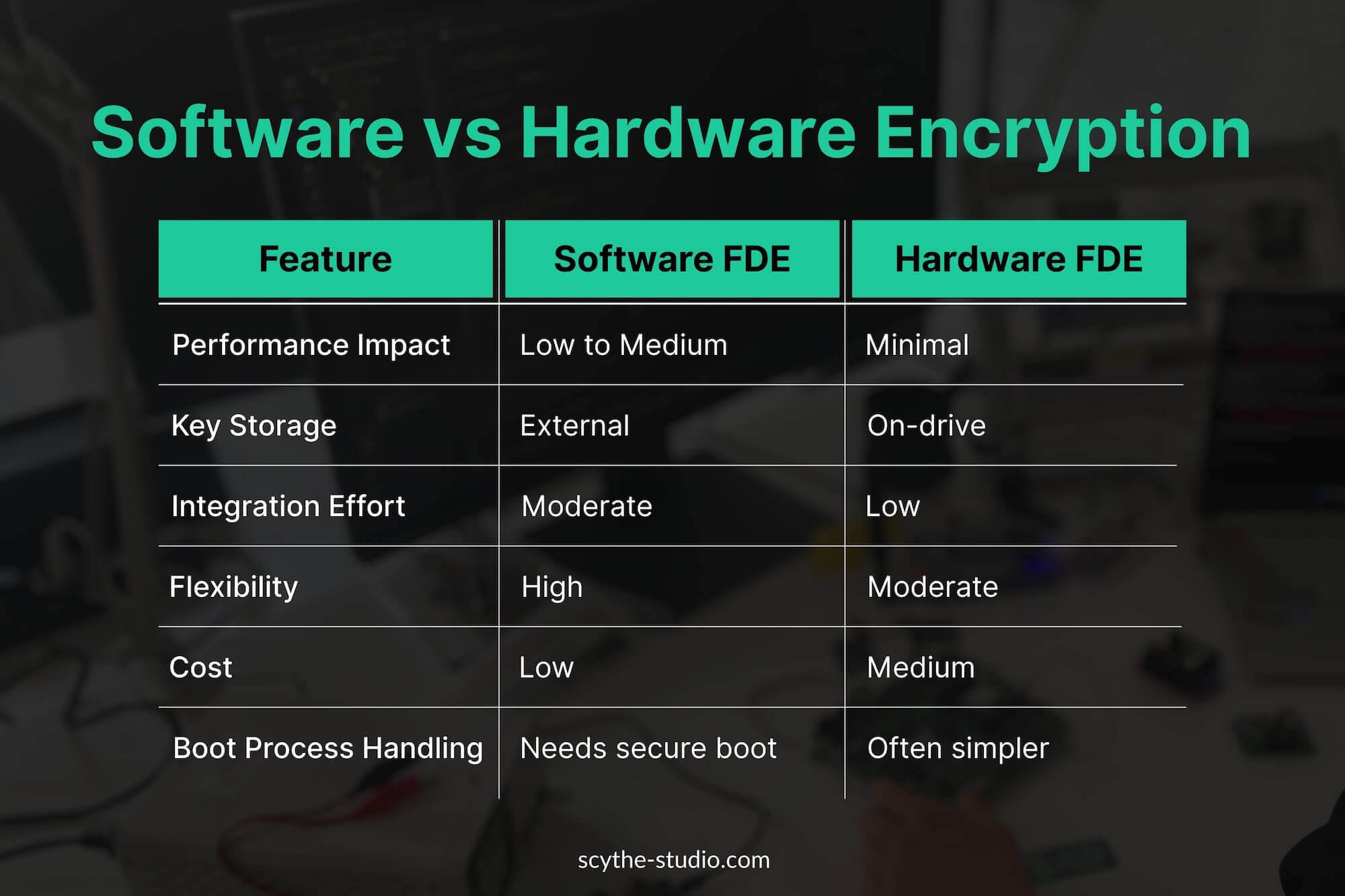
In practice, embedded device manufacturers choose an approach based on form factor and threat model. If a device can physically accommodate a standard SED (say a SATA or NVMe drive that supports Opal 2.0), using it can drastically simplify implementation – encryption is essentially built-in with little performance penalty. In fact, Opal 2.0 drives can encrypt all data without impacting performance, keeping data secure even if the drive is removed from the host device. However, not all embedded form factors support plugging in a commercial SED; many use raw flash or eMMC chips soldered on board. In those cases, software-based FDE (with the help of the device’s CPU or a dedicated crypto chip) is the way to go. The good news is that modern embedded processors often include cryptographic modules specifically for such purposes – for example, NXP’s i.MX series features a Cryptographic Accelerator and Assurance Module (CAAM) that can perform AES encryption and manage keys without exposing them to the CPU. Similarly, microcontrollers might have a hardware unique key burned into them, which can be used to encrypt the storage encryption key (i.e., the encrypted key never leaves the secure boundary), binding it to that device. These hardware assists ensure that even software FDE solutions have strong protection for keys and minimal performance impact.
One important aspect of FDE is managing the encryption keys. In a user-driven device like a smartphone or laptop, typically the user’s password is tied to the disk encryption key (either by deriving the key from the password, or by protecting the key with the password). Embedded devices, however, are often unattended – they boot up on their own after power loss or reboot, without a user present to enter passwords. How do they unlock their encrypted disks? This is usually solved with either secure key storage on the device or remote key provisioning.
Many embedded systems include a hardware element such as a Trusted Platform Module (TPM) chip, a secure enclave, or the aforementioned SoC key (like a fused HUK). These components can store the encryption key (or an unlocking key) in a tamper-resistant way. When the device boots, the secure element releases the key only if the system’s integrity is verified (for instance, the TPM may check that the system is in a known-good state via secure boot measurements). This binds the encrypted data to the device by ensuring only that hardware can access the same key needed to decrypt it: even if an attacker takes the storage out and places it in another system, it won’t decrypt, because the key is tied to the original hardware. The key never appears in plaintext on the main CPU or memory; decryption happens either within the secure element or the key is fed to the encryption engine only after proper authentication. This strategy allows devices to restart autonomously (for example after a power failure) and still maintain security, as the key can be unlocked internally without human intervention, provided all security checks pass.
In scenarios like distributed IoT systems, a device might fetch its encryption key from a central server at boot. The device would authenticate to a management service (e.g., via a public key-based certificate or secure token) and receive the disk key over a secure channel. This method requires network availability at boot and a robust infrastructure to manage keys, but it allows for centralized control – keys can be rotated or revoked from afar. Remote unlocking is used in some high-security environments where the devices are thin clients or sensors that are always online. If the device lacks connectivity or the management server is unreachable, local secure storage (like a TPM) is the preferred method.
Full disk encryption significantly elevates the security posture of embedded devices by mitigating a range of risks. Below are key security benefits and how they translate into risk reduction:
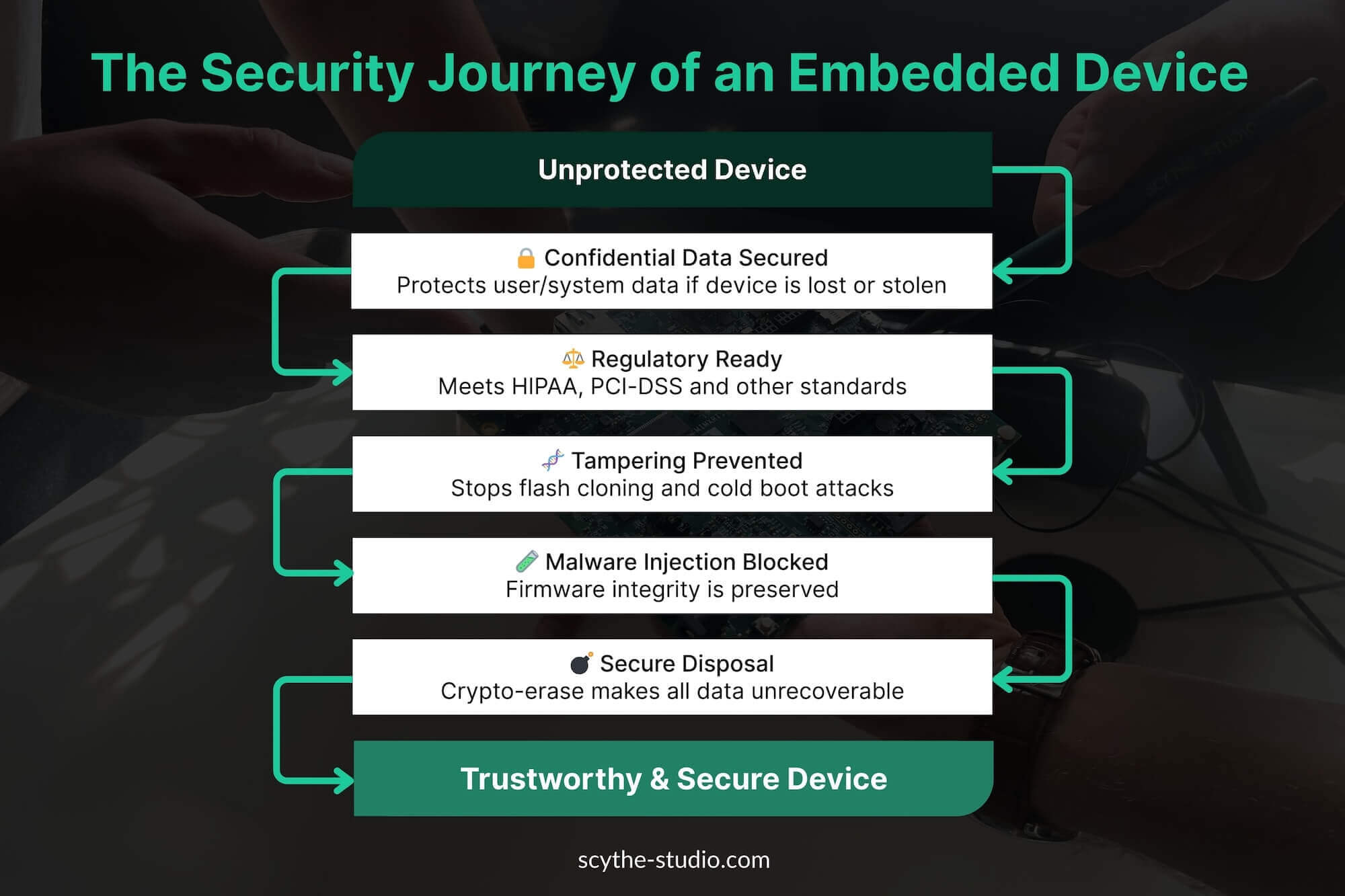
Implementing full disk encryption in an embedded device involves both technology choices and integration planning. Fortunately, the industry has developed several approaches to fit different needs, and many tools are available to ease deployment. Here we outline best-practice approaches and examples for incorporating FDE into embedded products:
While the technical aspects are important, the decision to implement full disk encryption in embedded products should be driven by the real business value it brings. By making security a core feature of your devices, you address risk management and customer confidence and market differentiation. Here are the key ways FDE adds value from a business and customer perspective.
Data breaches are expensive – $3.92 million per incident – and that includes not just legal fines but also loss of customer trust. In industries like healthcare and finance, showing your device encrypts all sensitive data can reduce liability insurance premiums and regulatory penalties, directly impacting your bottom line.
End customers, whether consumer or enterprise, want to know their products will keep their data safe. By advertising and delivering full disk encryption as a feature, you’re telling customers you prioritize security. Trust is a currency in B2B and B2C relationships and strong security is a way to earn it. That means not just customer satisfaction but potentially the ability to charge a premium for a security-hardened device or access market segments (like government or defense) that require encryption.
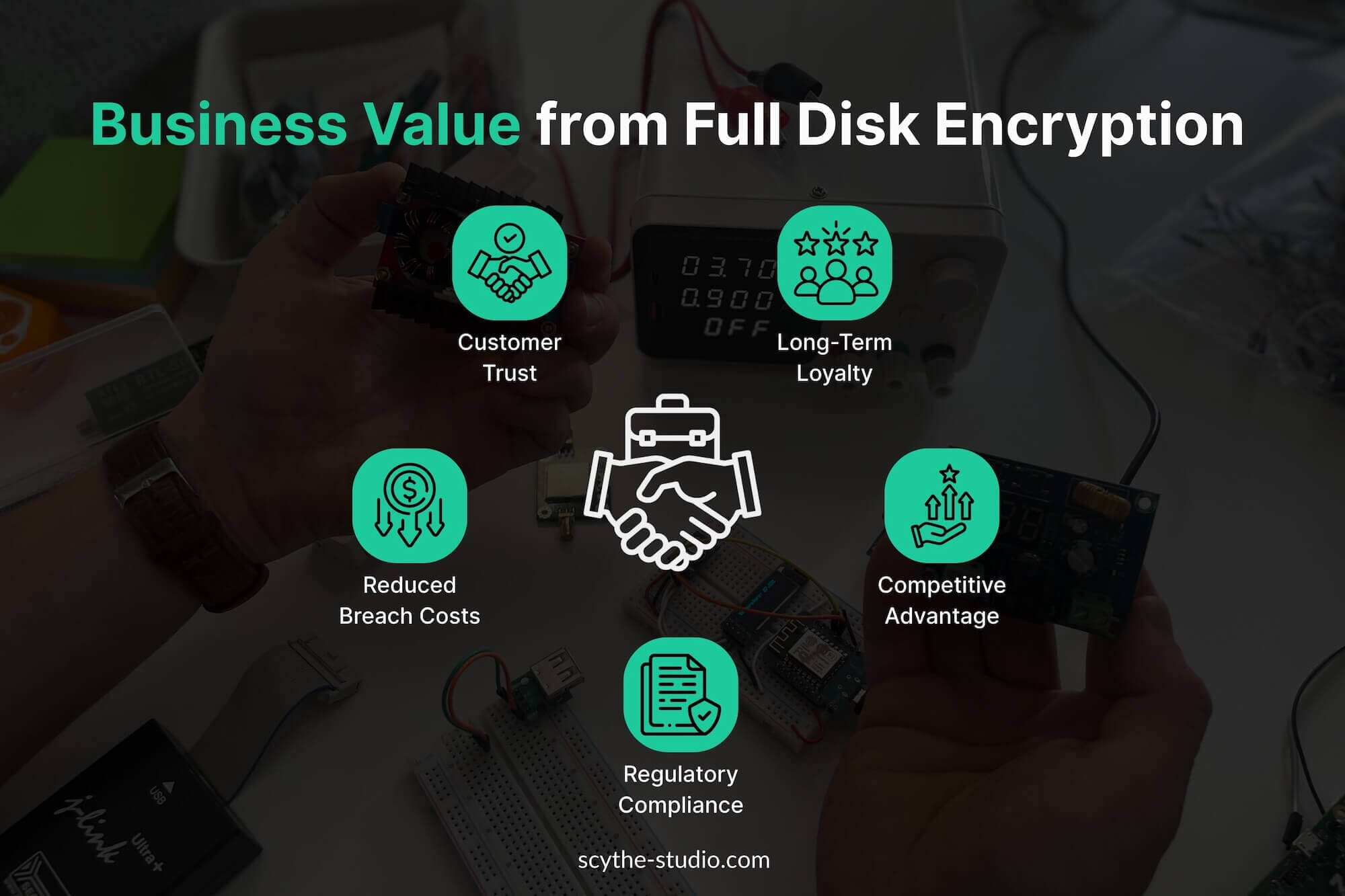
In a crowded market, products that can claim strong security stand out. When security incidents make headlines regularly, offering a solution that addresses those concerns proactively can be a major differentiator. You can position your use of full disk encryption as part of a broader “security by design” philosophy. That attracts security-conscious customers and preempts objections during the sales process.
Security features have a long tail of benefits. If your devices are secure over years, customers are less likely to experience incidents that cause them pain or force them to replace your solution. By avoiding security failures, you retain your customers and enhance your reputation in the market. Those satisfied customers become repeat buyers or even advocates. In some industries, an unblemished security record is a requirement to stay in business – and FDE is one of the tools that helps keep that record clean.
From a business perspective, full disk encryption in embedded systems is more than a technical tick box. It protects value across multiple fronts: it protects the value of data (often called the “new oil” in the digital economy), it protects the value of your brand and customer relationships and it adds value to the product itself. The relatively small investment in encryption pays back in trust, reduced risk and market appeal. For decision makers deciding where to invest in product development, FDE is a high return on investment in the world of cybersecurity features. It aligns the company’s interests (avoiding losses and attracting customers) with the customer’s interests (keeping their data safe) which is the hallmark of a win-win value proposition.
Embedded full disk encryption has become an essential part of any organization’s security strategy for devices outside the perimeter. It addresses a fundamental vulnerability – the data at rest – with simplicity: by making data, if accessed without authorization, worthless to the attacker. From a cybersecurity perspective FDE turns an embedded device from a weak link into a strong asset. From a business perspective it’s a sensible investment that protects your operations from breaches and boosts your credibility with customers. In an era where data breaches can kill a business, measures like full disk encryption are not just IT decisions but business imperatives.
For companies developing embedded software and systems, embracing full disk encryption and related best practices (secure boot, TPM integration etc.) is a clear signal of commitment to security. You can deliver devices that users can trust even in the worst case scenario. Whether it’s a smart appliance in the home, a medical device in the hospital or a drone in the field, the data it holds is safe from prying eyes and misuse thanks to strong encryption. Decision makers can confidently market this feature knowing it brings concrete risk reduction and customer value. In summary embedded full disk encryption makes products safer and businesses stronger.
By making full disk encryption part of your embedded devices you’re not only mitigating today’s risks but also future proofing your devices against the changing threat landscape. It’s a base upon which other security layers can be built. For any organization that values its data and its customers that base is worth the investment. In the end full disk encryption in embedded systems is about embedding trust into your devices – and there’s nothing more valuable in business than that.
Let's face it? It is a challenge to get top Qt QML developers on board. Help yourself and start the collaboration with Scythe Studio - real experts in Qt C++ framework.
Discover our capabilities
From medical devices and smart vehicles to industrial controllers and consumer electronics, embedded systems are everywhere—and increasingly connected. But with […]
Hey, welcome back to another blog post. Today we’re going to talk about the new Qt WebAssembly. This post will […]

Users of embedded devices – from industrial controllers to consumer electronics – are often unaware of hidden vulnerabilities that threaten […]